Pcapteller is a tool that allows the customization and replay of recorded network traffic. Mainly, the tool can help blue teams training their network security monitoring skills, by reusing resources already available on the Internet (e.g. PCAP files).
The tool also helps increasing the degree of realism of the scenarios included in the PCAPs, since blue teams can customize the network traffic before it is injected into the network.
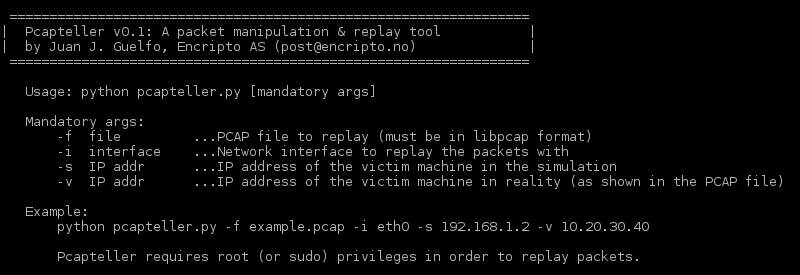
Pcapteller is written in Python 2.7. For this exercise, we will use Kali Linux as base operating system. Running the tool at once should present you some information about the expected arguments.
python pcapteller.py
In order to illustrate how the tool works, let me use a PCAP file from malware-traffic-analysis.net that contains an attack scenario involving an exploit kit delivering ransomware. This PCAP file describes a chain of events where host 192.168.122.70 is the victim.
Let us consider a case where a blue team would like to use such resource for a training session. The team is interested in using its current security countermeasures and configurations in production. The production network is using a class B internal IPv4 addressing schema (172.31.0.0/16). For this example, the victim machine will be 172.31.10.11.
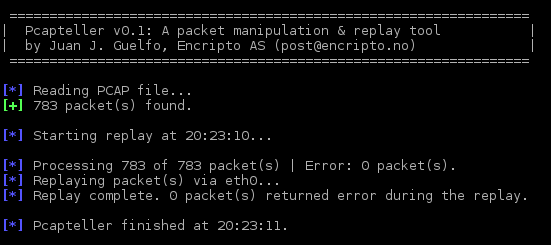
We can customize and replay the network traffic contained in the PCAP file with the following command:
python pcapteller.py -f 2015-05-14-Angler-EK-delivers-ransomware.pcap -i eth0 -s 172.31.10.11 -v 192.168.122.70
In such command, the arguments are understood as follows:
-f provides the original PCAP file that we would like to replay.
-i specifies the network interface that we would like to use. The traffic will be injected into the network via such interface.
-s specifies the IP address that we want to set as victim while replaying packets.
-v provides the real IP address of the victim, as seen in the original PCAP file.
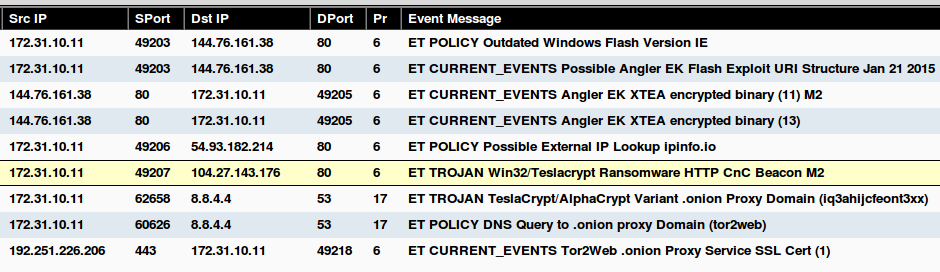
The result of the customized traffic injected by Pcapteller is described in the screenshots below.
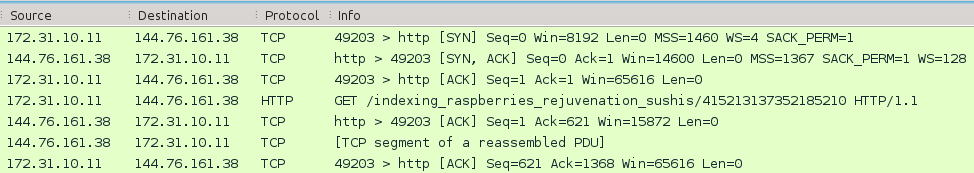
Fragment of the replayed network traffic seen from Wireshark. The victim IP address has been customized for the exercise.
Since Pcapteller injects the manipulated network traffic into the production network, existing security countermeasures can detect and alert about possible threats. This example shows how an Intrusion Detection System (Snort with ET GPL ruleset) would react to the manipulated traffic.
This example has illustrated how easy it is to customize existing PCAP file resources in order to make a realistic training session with reduced costs and risk. Pcapteller is at this point in an early stage of development, but new possibilities will come as soon as new features are implemented.