«I see dead people… walking around like regular people». With these words, a very young Haley Joel Osment began to tell Bruce Willis his scary secret in The Sixth Sense. That movie scene is in fact an analogy that some network security analysts may relate to. Concepts like network traffic replay could provide a similar effect, seen of course from a traffic analysis perspective. This post will go deeper into this idea, and it will propose a method for creating a network decoy during Red Team engagements.
Training your network security analysis skills and keeping your knowledge up to date is paramount, whether you are part of a seasoned Blue Team, or just a person entering network security analysis for the first time. However, finding or setting up low-cost, low-risk realistic scenarios might not be as easy as one would imagine. On November 2015, Encripto published a paper proposing network analysis training methods based on adversary replication, that could allow organizations to conduct effective and realistic network security analysis training sessions, while keeping costs to a minimum.
For those who would like to train and improve their network analysis skills, Encripto has released Pcapteller v1.0. This is a tool designed for traffic manipulation and replay. Version 1.0 implements new packet manipulation features, which extend the possibilities when re-creating network traffic scenarios. Feel free to read these blog posts if you want more information about the tool.
Despite Pcapteller aims for Blue Teams, it could also become a powerful resource for Red Teams. In such context, Pcapteller could assist with the creation of a network decoy during an engagement.
Let’s consider advanced security assessments that result in access to the target’s internal network. Such access could be obtained in multiple ways, for example by using social engineering against employees, compromising weak internet-facing systems, or just as starting point if the engagement assumes compromise.
In environments with tight network countermeasures and a (proactive) Blue Team in place, the Red Team must measure their movements across the target network, in order to fly under the radar. But, what if this is not possible? What if the Red Team needs to perform actions that could potentially draw the Blue Team’s attention?.
Creating a network decoy
Using Pcapteller in combination with VPN pivoting, a Red Team could create a network decoy. In other words, this could make a Blue Team see ghosts, like Haley Joel Osment in The Sixth Sense. Here you have an example on how this works in practice:
1. Assumptions
Let’s assume that the Red Team has already deployed a VPN tunnel towards the target network. The Red Team has also some basic target network visibility. In other words, they know about MAC addresses / IP address schema of the target network.
For the sake of this blog post, I will assume that the target network is 192.168.1.0/24, with a Palo Alto appliance (MAC address 00:1b:17:00:00:02) as gateway. The target network is also running Snort as Intrusion Detection System.
The Red Team has also downloaded a pcap file from malware-traffic-analysis.net, or some other awesome source. The pcap file should contain the chain of events and the network indicators related to an exploit kit attack with a successful ransomware infection.
Alternatively, network traffic with custom indicators could be generated and captured with other tools, such as Maligno and Wireshark. You may learn more about this topic by watching the Maligno Video Series.
2. Preparing your ghosts
Based on information gathered during the engagement, the Red Team should pick a set of MAC addresses that fits the target environment. The same applies to internal IP addresses that may be used as decoys, in an attempt to draw the Blue Team’s attention.
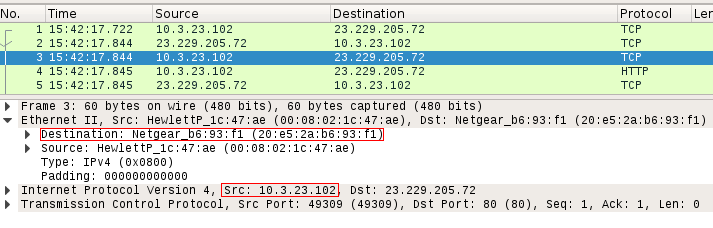
In this specific example, the pcap file downloaded from malware-traffic-analysis.net shows host 10.3.23.102 as victim. The MAC address of the gateway used by such host is 20:e5:2a:b6:93:f1.
3. Sending traffic
In order to deploy a realistic decoy that can drive network countermeasures crazy, and hopefully confuse the Blue Team, the Red Team will manipulate and replay traffic with Pcapteller over the existing VPN tunnel. In this case, the original host under attack will be replaced with 192.168.1.111 (a random host in the target network), and the original gateway’s MAC address will be replaced with the Palo Alto appliance’s 00:1b:17:00:00:02.
With such decisions made, Pcapteller can be run like this:
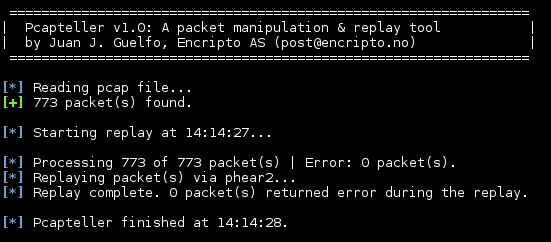
python pcapteller.py -f example.pcap -i phear2 -a 20:e5:2a:b6:93:f1 -b 00:1b:17:00:00:02 -c 10.3.23.102 -d 192.168.1.111
This will manipulate and replay the contents of «example.pcap» over the VPN tunnel interface «phear2». Pcapteller should replay the traffic quickly, resulting in something like this:
4. The results
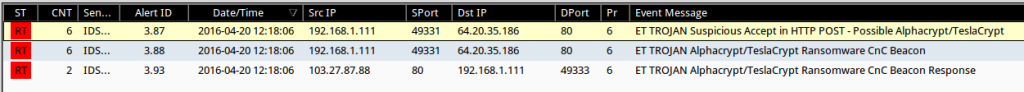
Once the network traffic is replayed over the VPN tunnel, the countermeasures placed on the target network should register the «fake activity».
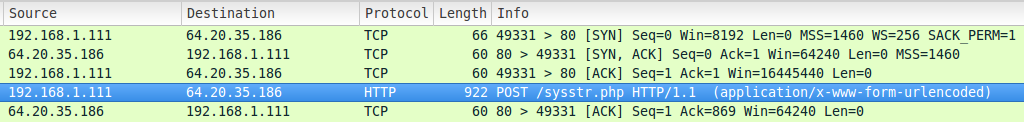
Even if the Blue Team goes into a packet level, Wireshark will display the replayed traffic as if the infection really happened. The traffic should reflect the manipulation of both MAC and IP addresses:
How can you tell?
The network decoy created by Pcapteller is not perfect. This means that a network analyst could eventually detect the network decoy and realize it was just a diversion. Depending on the analyst’s view of the network and his/her experience, that conclusion could be found sooner or later.
In The Sixth Sense, a very young Haley Joel Osment told Bruce Willis a secret. He realized that dead people was walking among the living. As a network security analyst, How can you tell whether you are seeing real traffic, or a «ghost»?
Feel free to send us your answer!