Did you know that the Blue Team Training Toolkit (BT3) also is a powerful resource for red teams?
This blog post will demonstrate how BT3 modules can assist with the production of network indicators, or decoys during a red team engagement.
In environments with tight network countermeasures and a (proactive) blue team in place, red teams must measure their movements across the target network, in order to fly under the radar. Occasionally, red teams may perform actions in the network that could draw a blue team’s attention.
By using BT3 in combination with VPN pivoting, red teams can create a network diversion. In other words, they can make a blue team see ghosts, letting their red team hide in plain sight.
How to Create a Network Diversion
Let us consider an advanced security assessment that results in access to the target’s internal network. The environment has tight network countermeasures and a proactive blue team in place. It is not possible for the red team to fly under the radar. It therefore needs to perform actions that could potentially draw the blue team’s attention.
By using BT3’s Pcapteller module in combination with VPN pivoting, a red team could create a network diversion. In other words, this could make a blue team see ghosts through packet captures and/or deployed Intrusion Detection Systems. Here you have an example on how this works in practice:
Step 1: Assumptions
Let’s assume that the red team has already deployed a VPN tunnel towards the target network. The red team has also some basic target network visibility. In other words, they know about MAC addresses or the IP address schema of the target network.
For the sake of this explanation, the target network will be “172.16.50.0/24”, with a Palo Alto appliance (MAC address “00:1b:17:00:00:02”) as gateway. The target network is also running Snort as Intrusion Detection System.
The red team has also a PCAP file containing the chain of events and the network indicators related to an exploit kit attack with a successful ransomware infection. Alternatively, network traffic with custom indicators could be generated and captured with other tools, such as BT3’s Maligno module and Wireshark.
Step 2: Preparing your ghosts
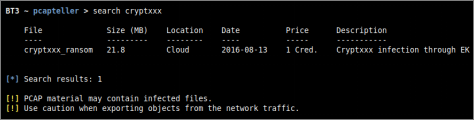
Based on information gathered during the engagement, the red team should pick a set of MAC addresses that fits the target environment. The same applies to internal IP addresses that may be used as decoys, in an attempt to draw the blue team’s attention. In this specific example, the premium training material “cryptxxx_ransom” will downloaded from the BT3 cloud and later used during the case.
The original PCAP file shows host “192.168.1.4” as victim. The MAC address of the gateway used by such host is “00:1f:33:c3:43:34”.
Step 3: Sending traffic
In order to deploy a realistic decoy that can drive network countermeasures crazy, and hopefully confuse the blue team, the red team will manipulate and replay traffic with BT3’s Pcapteller module over the existing VPN tunnel.
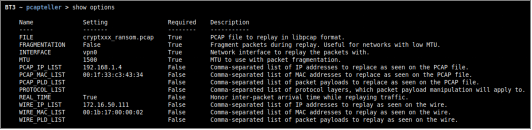
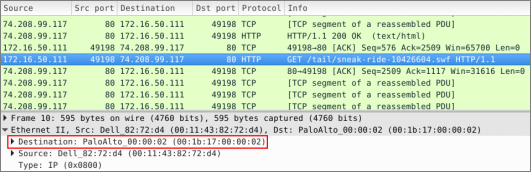
In this case, the original host under attack will be replaced with “172.16.50.111” (a random host in the target network), and the original gateway’s MAC address will be replaced with the Palo Alto appliance’s “00:1b:17:00:00:02”. All manipulated traffic will be replayed over the VPN tunnel interface “vpn0”. With such decisions made, Pcapteller can be configured like this:
For even a more realistic look, “REAL_TIME” support will be enabled on Pcapteller. This will honor inter-packet arrival time during the actual replay.
Step 4: Results
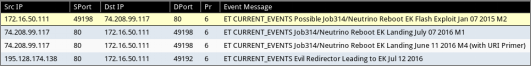
Once the network traffic is replayed over the VPN tunnel, the countermeasures placed on the target network should register the “fake activity”.
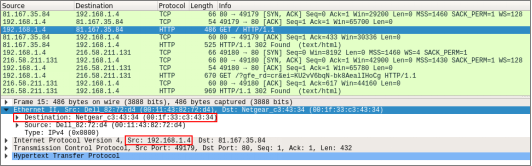
Even if the blue team goes into a packet level, Wireshark will display the replayed traffic as if the infection really happened. The traffic should reflect the manipulation of both MAC and IP addresses.
Check out the BT3 user guide, or the Blue Team Training Toolkit Video Series for practical examples.
You can also download the Blue Team Training Toolkit and test it for yourself!