Blue Team Training Toolkit (BT3) is software for defensive security training, which will bring your network analysis training sessions, incident response drills and red team engagements to a new level.
BT3 includes the module Maligno, which allows you to simulate malware infections or targeted attacks with specific C&C communications in a safe manner.
This blog post will illustrate how to setup Maligno with a practical example.
Practical Example
In this case, Maligno will be used during the simulation of a targeted attack. A piece of malware known as “Havex” or “Oldrea” has been actively used against western energy companies in the past.
Symantec has documented several cases in a report that describes network indicators associated with Havex. BT3 includes a Maligno malware indicator profile based on such report, and it will mimic the malware’s network behavior without risking any infection.
Before starting the actual setup, this case will assume that a blue team has already deployed some minimal infrastructure for network traffic monitoring. In addition, Snort with ET GPL ruleset will be used as Intrusion Detection System.
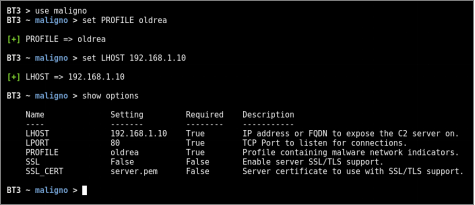
- Step 1: Configure the module options
In this case, the “oldrea” profile should be configured as well as the server’s IP address. Communications will go over HTTP and they will use the standard port TCP 80 (default).
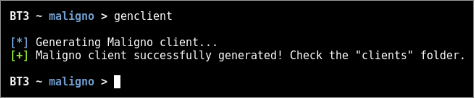
- Step 2: Generate and deploy your Maligno client script
A Maligno client script should be successfully generated once the module has been configured. Client scripts should be then deployed on those hosts that will simulate the infection or should be considered as compromised.
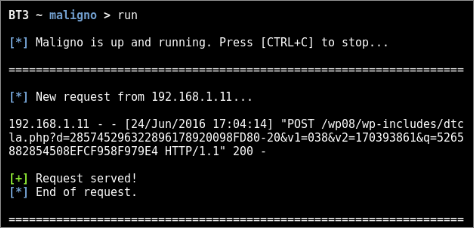
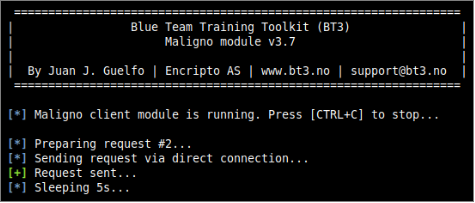
- Step 3: Start the server and run the client
The Maligno server component can be started directly from BT3’s interactive interface. The Maligno client, on the other hand, should be invoked from the machines where the scripts were deployed.
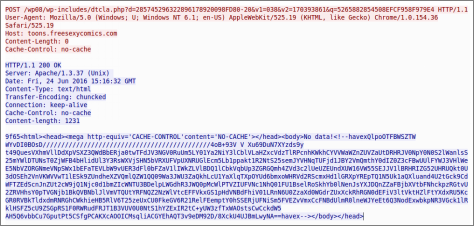
- Step 4: Traffic analysis
The network communications should present patterns based on the malware indicators configured in the profile. Network equipment and packet captures should register the activity at this point.
Check out the BT3 user guide, or the Blue Team Training Toolkit Video Series for practical examples.
You can also download the Blue Team Training Toolkit and test it for yourself!